Introduction
A key consideration when designing wireless networks for large venues is ensuring that all appropriate steps are taken to maximise airtime efficiency.
Multipurpose facilities, with a diverse range of use cases, often find SSID consolidation challenging due to a requirement for macro or micro-segmentation of user data traffic, usually driven by the need for compliance, such as PCI DSS or access to headend devices from remote locations over a wireless medium. This, in turn, creates a demand for unique SSIDs for each use case.
The impact of not addressing this has been demonstrated in similar venues, where venue integrators, if not given proper provision for network access, would circumvent the building network and implement independent ad-hoc wireless systems, often creating destructive sources of interference such as CCI, OBSS, and ACI.
The following key objectives were defined.
Requirements
- Implementation of a single SSID for landlord, contractors and venue integrators.
- Improve airtime efficiency of the wireless system.
- Lateral threat mitigation, increased data confidentiality and integrity.
- Establish a Single policy decision point (PDP)
- Establish a Single policy enforcement point (PEP)
A converged 802.1x solution was proposed for user authentication and a single SSID broadcast covering all use cases.
Other options, such as iPSK, were considered but ultimately rejected due to the risk of PSKs being compromised and the necessity of maintaining a database of client MAC addresses, which are combined with the PSK for policy assignment based on endpoint identity groups.
These issues are further compounded by the requirement from many mobile vendors to begin enforcing MAC rotation, thus making the solution difficult to scale without incurring significant administrative overhead and requiring additional training for end users to disable such features upon their first association with the network.
Solution Design
For the 802.1x implementation, policy enforcement and identity management would be centralised using a combination of Microsoft Windows Active Directory and Cisco Identity Services Engine. A public certificate would be installed on the AAA server to eliminate the need to manage client-side certificates throughout the venue lifecycle.
Service partners were grouped based on the required network access privileges, which were mapped to Windows security groups and individual user accounts defined within each group.
Authorisation profiles established on the AAA server would assign network roles based on security group membership at the point of authentication. This would enable the automatic provisioning of DACLs and VLAN assignments to achieve macro and/or micro segmentation where necessary. Additionally, partner networks would also group into VRFs, with inter-VRF traffic scrubbed through an internal firewall pair.
This is summarised in the following diagram.
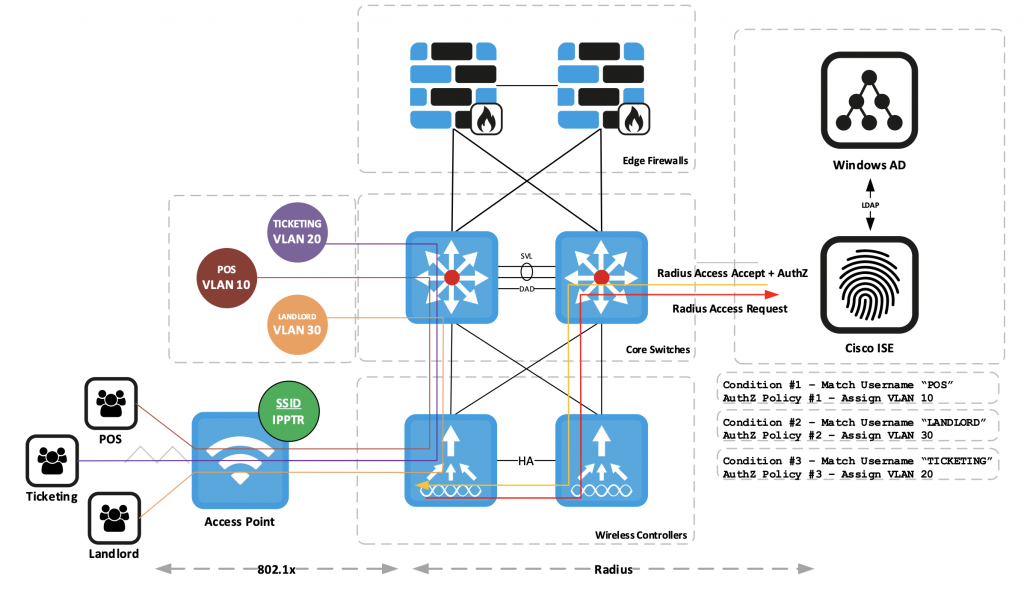
Figure 1 Policy assignment based on user identity
Security Considerations
EAP-PEAP was chosen as the Layer 2 authentication protocol and MS-CHAPv2 as the inner method. Together, they support mutual authentication, dynamic key generation, strong credential security, and are widely supported by client vendors. If configured correctly, this ensures the broadest range of interoperability while still ensuring data confidentiality, integrity, and robustness.
Certain risks were identified prior to implementation, such as the susceptibility to Evil Twin / Rogue AP Attacks when not choosing to validate the server certificate, and cryptographic weaknesses in MS-CHAPv2.
These risks were presented to the client, but the decision was made to proceed as the trade-off in terms of practicality outweighed the benefit of managing user identities centrally and avoiding the need for multiple PSK networks.
In this instance, due to the absence of an MDM to manage client certificates or profiles, and a need to support all 3rd party devices, a publicly signed digital certificates was provisioned on the AAA server, however this posed an additional challenge as by default many public CA root certificates do not exist with the default trusted store on the majority of devices tested.
Vendors such as Apple publish these and the associated serial numbers. Still, the client’s chosen CA, GoDaddy, was not able to provide a certificate signed by one of the trusted root or intermediate CAS. Thus, clients were presented with a certificate warning on first association.
Server-side certificate validation behaviour differs between vendors. Some make it a mandatory requirement, while others allow you to selectively disable it.
As an additional measure, each device is configured with a fallback PSK profile. The associated SSID is left disabled but can be enabled at short notice in the unlikely event that the public certificate is revoked or expired, minimising risk of a service impact for the venue.
Validation and Testing
For business-critical client devices, e.g., POS, certification and validation was enforced to ensure that they were subjected to testing before being brought onto the production network. Firstly, this required that they be Wi-Fi Certified and recognised using their product finder tool.
The second stage was to conduct a device capability assessment.
- The device is profiled using a WLAN Pi (Profiler App) to validate radio and client capabilities referenced against vendor documentation.
- Device is associated with a test AP using a security profile configured by the owner/stakeholder, using both supported EAP methods applicable to the device on test and vendor-recommended software, drivers, or firmware.
- Feature interoperability testing is conducted to validate support for 802.11 amendments 802.11r, 802.11k, 802.11v, 802.11w, and 802.11e.
The third stage is to ensure that all client devices, once profiled, meet the minimum connectivity requirements, as defined below. This is important to ensure that the wireless network, as deployed, does not need to deviate from standard to accommodate less capable devices.
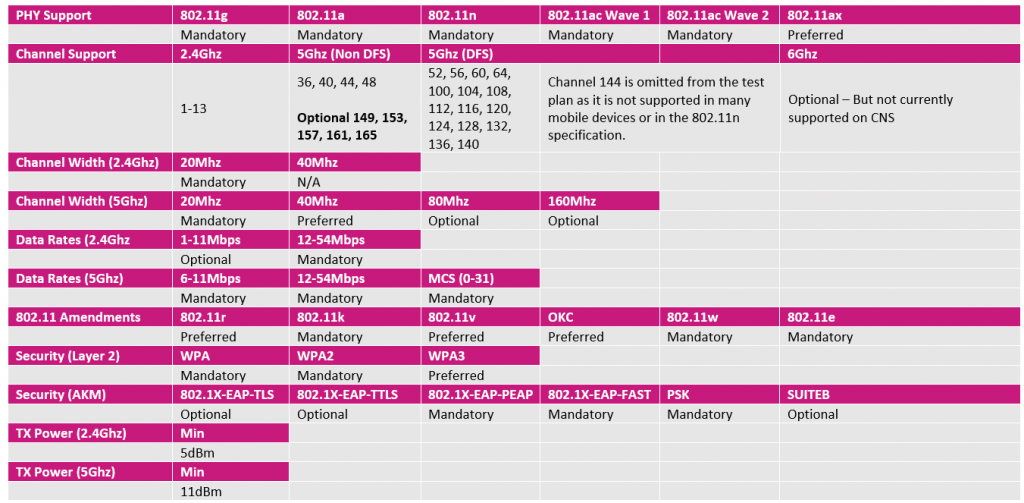
Once all requirements have been met, the device is approved for use on the production network and released to the end user.
Summary
The implementation of a converged 802.1x solution has reduced the need for third parties to create ad-hoc wireless networks, minimised the number of unauthorised access points within the venue, and established a unified point for identity management and access control. This approach has proven invaluable for managing wireless contention, enhancing operational security, enforcing policies, and decreasing administrative burdens for IT staff.